Updated: September 2, 2009
Welcome to the second article on encryption!
In the first article, we learned how to use encryption software to secure individual files. This method proved quite easy to master, as our tools merely required that the user right-click on the target file and choose whether to encrypt or decrypt it. However, while file encryption works well with a small number of files, it does not scale well against large repositories of data, involving thousands of directories and files, some which are important and some which are not. You can't possibly go through all of them and right-click each and every one, right?
Today, we will do just that - learn how to create encryption volumes, large encryption containers that can store multiple files and folders inside them.

What is volume encryption?
Volume encryption is a method that allows you to create encrypted containers inside which you will be able to store your data. The containers themselves can be files, partitions or even whole disks. Their size will vary depending on your needs and physical limitations of your storage devices.
The encryption contains are quite useful and easy to manage, because you treat them as separate entities. For all practical purposes, these containers are virtual hard disk volumes. Think of your virtual containers are additional, on-demand disks that you connect when you need to work with the data stored on them, except you require a key to be able to see the data. The containers can be of any size and kept anywhere, which makes them useful for large-scale operations.
The downside of this approach is that the initial setup is more complex and requires some knowledge of the system internals and disk behavior. Moreover, opening and closing the encryption containers takes more than a right-click. Finally, if the container gets lost or damaged, there is a chance you may lose all data stored inside it.
Anyhow, for an introduction and more details about the differences between the two methods, you should read the first tutorial.
Tools of the trade
In the file encryption chapter, we used three different tools for the task, PGP, ccrypt and AxCrypt. ccrypt was a Linux-only tool and AxCrypt was a Windows-only tool, but the two offered pretty much the same functionality. PGP was available for both Windows and Linux; we will talk about it again in the third part of this series when we discuss mail encryption.
Today, we will use only one program: TrueCrypt.
Let's begin.
TrueCrypt
TrueCrypt is probably the most popular encryption software available. There are many reasons for that. First of all, it works well and it's free. Second, it is available for all major operating systems. Third, the software has a very high degree of portability, as its volumes can be placed anywhere. Moreover, the Windows version of the software can also run from portable devices, adding to the freedom and flexibility of use. Another great strength of the software is that it offers a large number of volume types and encryption modes, which makes it suitable for just about any user. Lastly, the software documentation is well written, step-by-step and laid out in a professional manner.
I have listed TrueCrypt both in my New cool list of Linux must have programs and my recent A-Z Windows guide, as it is a definite keeper for both Windows and Linux users.
Today, we will learn how to use TrueCrypt on both Windows and Linux. We will learn the differences between several encryption modes and different volume types. We will also learn about TrueCrypt portability and pay special attention to nuances between Windows and Linux versions. We will also discuss backups.
Note: TrueCrypt has a number of ultra-paranoiac features, including hidden volumes and whole-system encryption for Windows. Due to the very high potential of abuse of these methods and the very high risk of data loss involved due to accidental misuse, I will not demonstrate these techniques.
Now, let's start.
Since TrueCrypt can be slightly confusing to new users, we will start by installing the software and then using its volume creation wizard. We will explain different concepts as we go along. First, a demonstration on Linux, after that - Windows.
Linux
Install TrueCrypt
TrueCrypt will probably not be included in the software repositories, so you will have to manually download it from the official website. Choose the package for your distribution and download it.
The TrueCrypt executable comes inside a tar archive. So you will first have to extract the archive and then launch the installer.
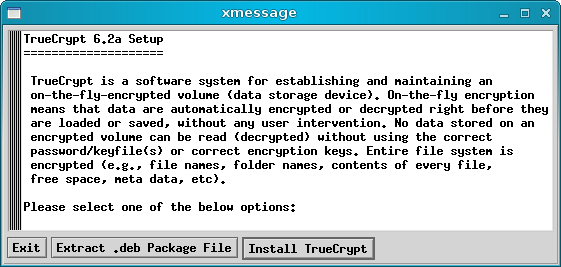
You will have to agree to a License:
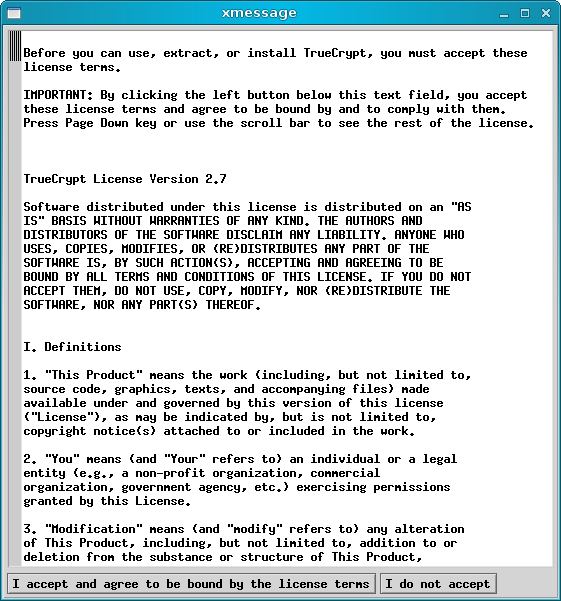
After that comes that standard installation of a package; for example, Gdebi handling a DEB package. On RedHat-based or SUSE systems, you will have an RPM installation.
And there you have the software running:
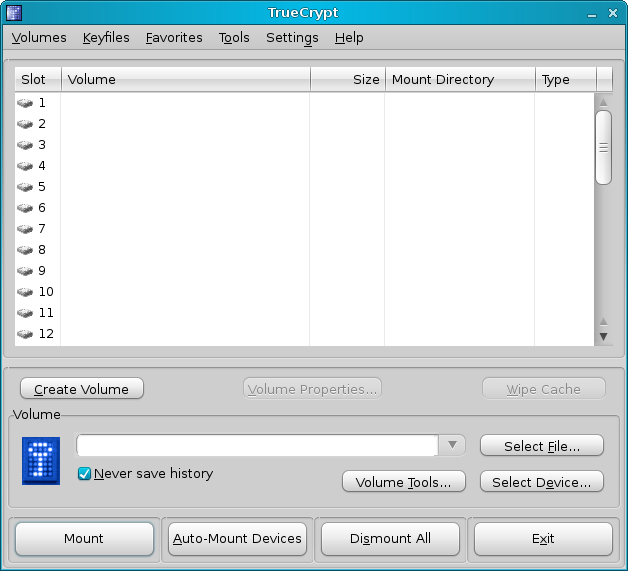
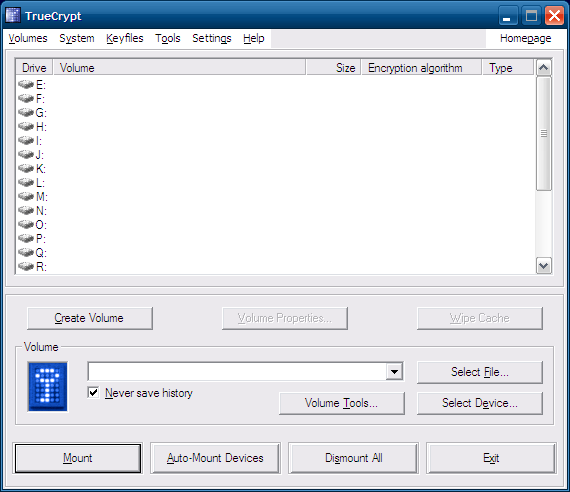
A brief overview of the main GUI:
The slots 1-12 are mount points to which you will be able to mount your volumes. The Mount Directory will point to the actual mount path on your system. The different buttons in the bottom half of the GUI allow you to mount (and auto-mount) and dismount existing TrueCrypt volumes. This is very similar to working with external USB devices, except that instead of plugging in and out physical hardware, you work with virtual devices that are the TrueCrypt volumes.
Using TrueCrypt
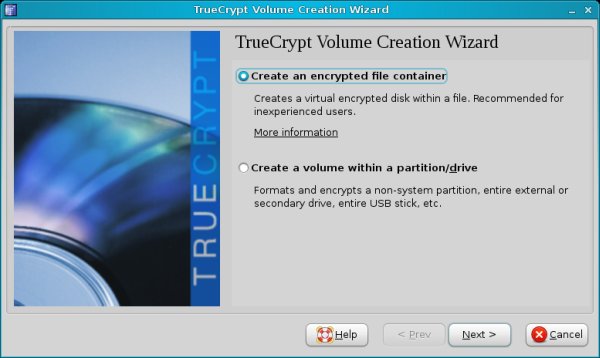
Now, it's time to start using TrueCrypt. Currently, we do not have any volumes, so our first step will be to create one. Click on Volumes > Volume Creation Wizard.
Volume types
Our first dilemma is where to use a file container or a partition/drive.
The easiest and simplest method is to create a file container and then use it as an the encryption volume. For example, you can create a 100GB file into which you can then store files and folders.
However, the notion of storing files inside what is essentially another file is a bit difficult to grasp for non-techies. But the volume file should not be treated as a ... file, simply because it is not usable by the system in any way. Only TrueCrypt can make any sense of this container and put it to good use. In fact, the program works by mounting the file volume to a directory path. After that, it becomes a normal part of the operating system and is used transparently just like any other path.
After the volume is dismounted, it becomes just another (unusable) file on your disk. The whole purpose of this file is to occupy space so that other programs cannot use it. You can think of file volumes as placeholders for encrypted data.
Note: On Windows, this takes form of drive letters. TrueCrypt mounts volumes to letters. After the mounting process is complete, you use the volume as drive G:, K: or any other.
The average-difficulty option is to encrypt entire partitions. Partition volumes then become raw devices that are inaccessible by the system. The simplest way to think of partition volumes is as unused space on the disk that you cannot access.
The average difficulty comes from the fact that the user must understand what partitions are and how they work and be aware that one of them (or more) is used by the TrueCrypt program. It is very easy to forget and format the supposedly empty partition only to remember later it was actually a TrueCrypt container.
Note: This is particularly true on Windows, where the operating system automatically suggests to format partitions that it cannot read, including TrueCrypt partitions. They will show up as drive letters, but when you try to click on them, you won't be able to open them. Instead, Windows will ask you to format them! It is quite easy to forget the partition is not empty and destroy the volume.
The most difficult option is to encrypt entire devices, like hard disks. The risk of destroying data is even more acute than with partitions, especially on Windows.
To make things simple, we will start with file containers.
Then, our next dilemma is whether to create a standard or a hidden volume.
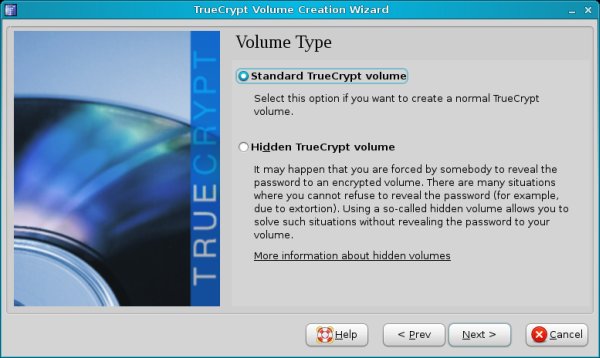
Hidden volumes are dangerous. This is because they are virtually invisible containers inside other TrueCrypt containers. Not only is this option totally unsuitable for new users, the risk of data loss is great. You can easily forget they are there and overwrite them. TrueCrypt does offer a number of precautions that can help keep hidden volumes safe from accidental damage, but the control is in the hands of a user.
Because of the associated risks, I will not demonstrate hidden volumes.
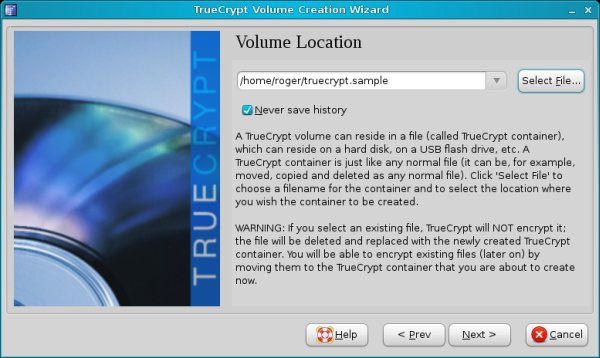
Location
Now comes the more routine selection of the volume location. Just choose any file name and place it anywhere you want on your accessible drives. You can even place it on external devices, if you want.
The operating system will treat the containers as files, albeit ones it cannot open, but you will be able to move, copy or delete them, just like any other file.
Encryption options, size & password
Choose the encryption algorithm, the volume size and the password. TrueCrypt recommends excessively long passwords and will probably warn you that your selection is too short or too weak. You can follow the advice and use a long, difficult password, but make sure you can remember it. Otherwise, your container will be useless.
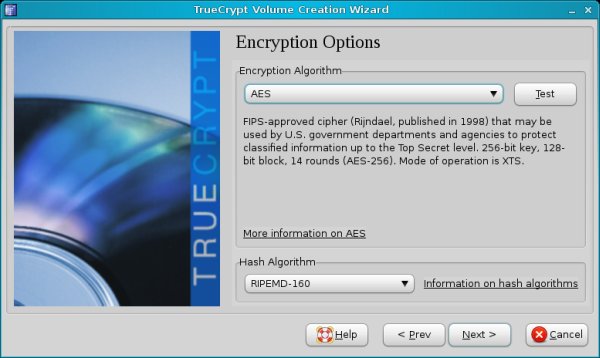
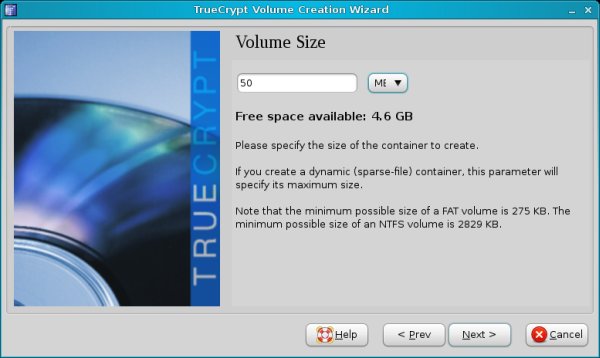
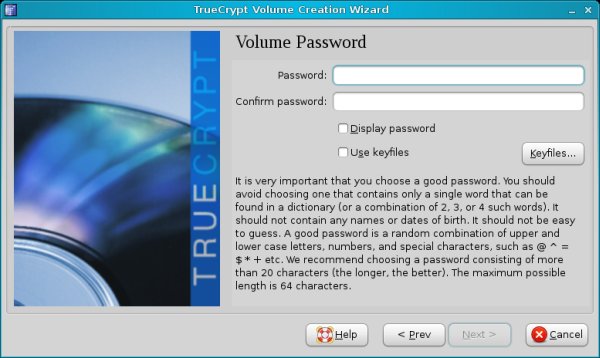
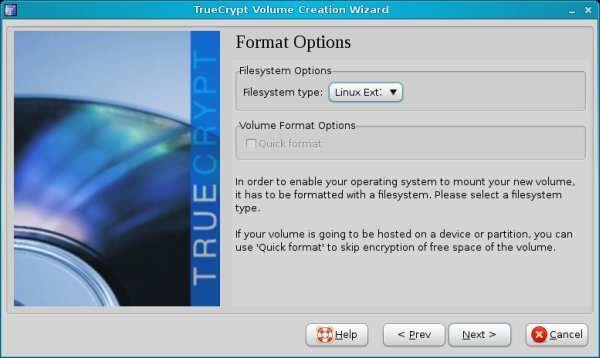
Now comes the interesting bit - formatting options. On Linux, you can choose FAT, Ext2 or Ext3. Your best choice is Ext3.
You will be asked whether you want to use the volumes on other platforms. This question should probably come before the formatting type, as it determines the filesystem choice.
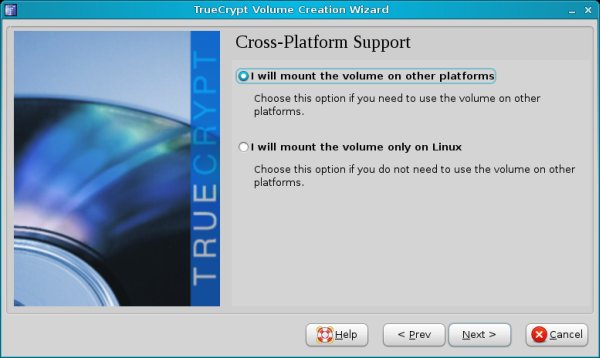
If you choose Ext2/3, you'll see a warning that other operating systems may not be able to read the volumes.
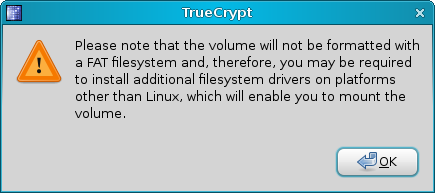
Compatibility
Now, I personally recommend you do NOT create TrueCrypt volumes on Linux if you're also using Windows. This is because you will have problems using these volumes on Windows. If you use FAT, you'll be using an old, inferior file system that does not handle large files well. And if you choose Ext2/3, you will need special drivers to be able to see them on Windows.
Instead, you should create the volumes on Windows and choose NTFS. This will allow best performance on Windows - but you will also be able to open them on Linux. If your distribution can read and write to NTFS partitions, you're all set.
Since Windows is the weakest link here, you need to align to it.
Now, let's see the creation through.
Once this is done, you can start using your new volume.
Mount & Dismount TrueCrypt volumes
To start using your volumes, click on Select File in the main menu. If you're using partitions or disks, click on Select Device.
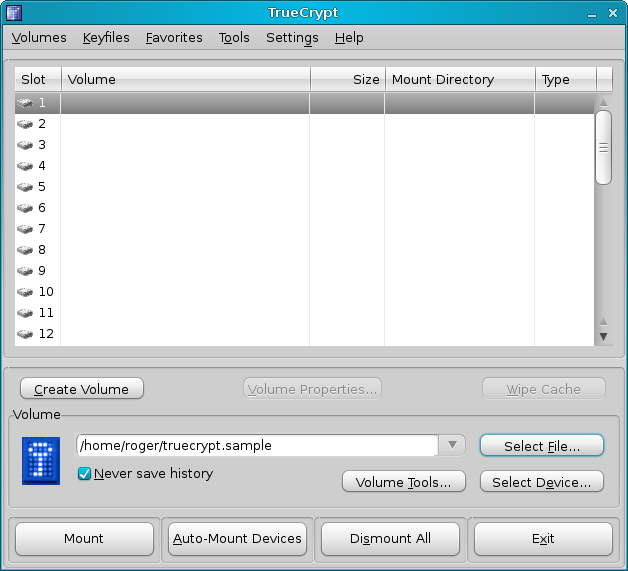
Provide the right password:
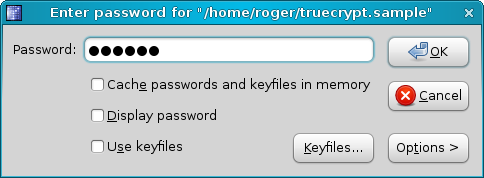
And that's it. You now have the volume mounted.
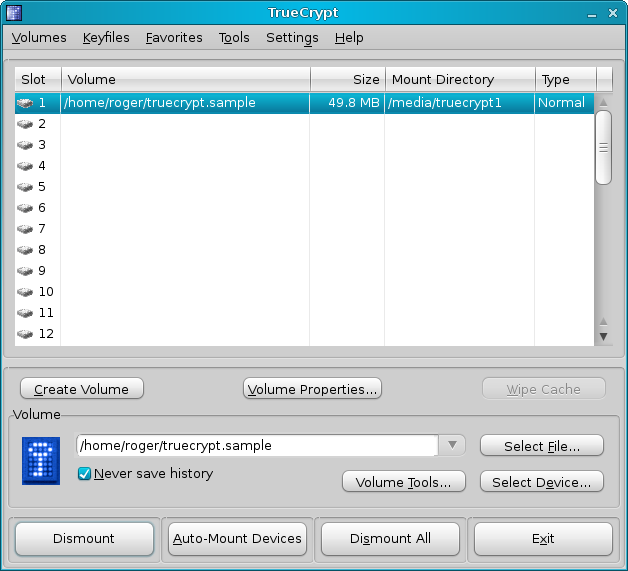
Notice the Mount Directory. It's under /media/truecrypt1 on the system. Very simple and neat. Just browse into this directory and use it as you normally would. Once you're done, click Dismount and the volume will be removed.
Very simple!
When should you use TrueCrypt?
TrueCrypt is useful when you want to create large encrypted containers into which to store data, without individually messing up with files and folders. The big advantage of this approach is that it allows you to handle TrueCrypt volumes as partitions or even whole disks, without worrying about the structure of content stored therein.
On the other hand, TrueCrypt requires a little more expertise to setup and use. Furthermore, you need to be aware that should you volume get damaged, all content within might be lost, as opposed to individually encrypted files. In fact, TrueCrypt volumes pose a single point of failure.
Therefore, it is critical to backup TrueCrypt volume headers, as they might help in recovering lost data from damaged containers.
Backup volume headers
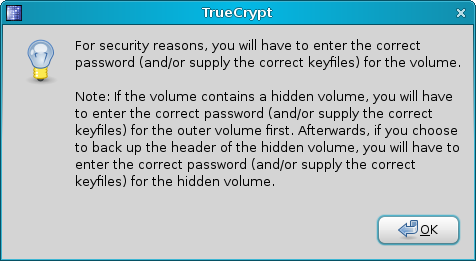
TrueCrypt allows you to backup your volumes. If they get damaged somehow, you'll probably be able to open them and save some of the data. This backup procedure is critical and should never be skipped. After you successfully create a new volume, the first thing you want to do is to backup its headers.
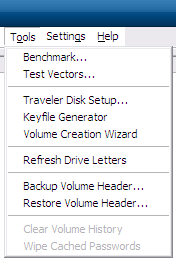
Go to Tools > Backup Volume Header.
Answer the short wizard:
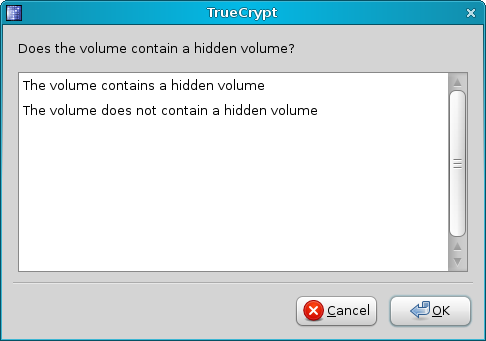
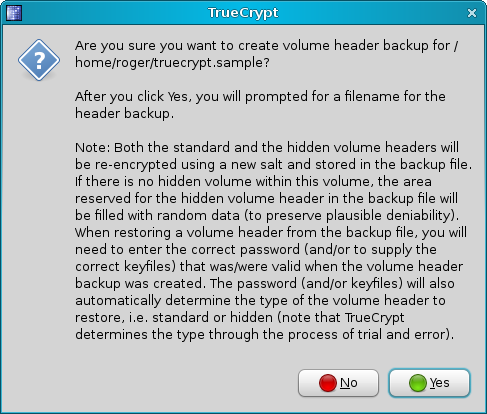
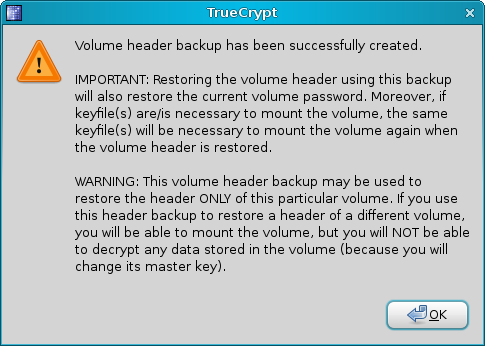
You should keep this backup in a safe place. First of all, it should definitely not reside inside the volume itself. You will probably want to keep it on a CD/DVD or a number of computers, to reduce the risk of loss or damage. Now, let's take a look at the Windows side of this great tool.
Windows
What we saw above holds 90% true for Windows. There are some small differences. We'll now review them.
Create new volume
On Windows, you have another type of volume available, whole system or whole disk encryption. This is a very advanced feature that requires creating new partitions or resizing existing ones, creating hidden volumes and many long hours of encrypting the system partition during the boot.
I can't begin to emphasize how risky this is, as less knowledgeable users can wipe their entire Windows installation if they are not careful. I will not demonstrate this feature here.
Whole system/disk encryption can be useful for laptops, though. Just make sure you're aware of the risks and know what to do if something goes wrong. If your system does not boot, what do you do? Live CDs won't help you now, as the system or the disk will be encrypted ...

Formatting options
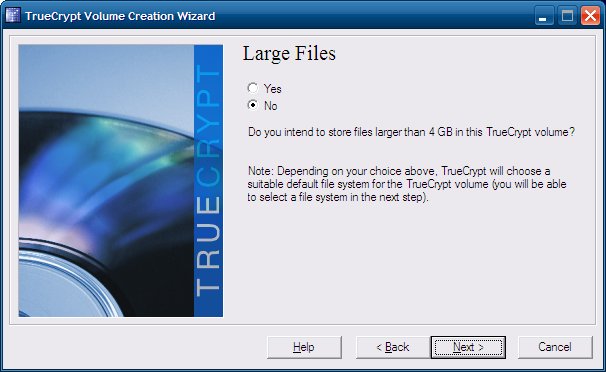
On Windows, the choice of filesystems will be different - FAT and NTFS. You will be asked if you want to use files that are larger than 4GB, in which case NTFS will be automatically selected for you.
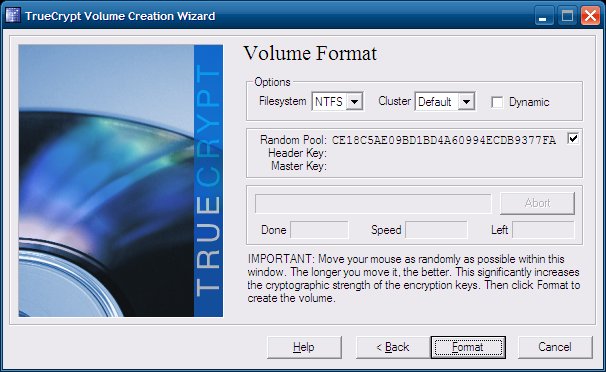
Backup
Backup remains the same, but it is important to mention it once again:
Portability
The Windows version also comes in a portable flavor. You can use the PortableApps version or create your own. Instead of installing TrueCrypt, just extract the package to its own directory.
We have already talked about when you should use TrueCrypt, so this pretty much concludes this article.
Conclusion
Today, we have learned how to use the powerful, versatile TrueCrypt software to create encrypted volumes that will hold our data and keep it safe from undesired access. Most importantly, we learned the subtle differences between different encryption modes and types, the formatting options, the cross-platform compatibility, and how to safely backup our volumes. We also touched the portability features.
This second article on encryption now provides you with yet more tools to maintaining the privacy and integrity of your data. In the third article, we will talk about emails.
I hope you liked it. Have fun and enjoy yourselves.
Cheers.