Updated: November 22, 2017; November 23, 2017
Firefox 57 is out. And so is Noscript Security Suite 10, the first WebExtension version of this highly popular and successful Firefox addon. The redesigned addon brings in a whole range of changes and frustrations. So if you feel surprised, taken aback or just confused by the way Noscript works post 5.x series, I will try to unravel some of the fog in this tutorial.
Please note that this is the first edition of this guide - there will be updates and follow ups, as Noscript will inevitably change and improve. I will try to provide the simplest explanations and hints, so that your journey, and mine, can be more pleasant. I believe Noscript is an essential part of the Web, the primary reason to still stick with Firefox, and this is why I decide to compile this howto. Follow me.
Noscript at a glance
The new UI is completely different from the previous 5.x series. The old, classic Noscript had a vertical hierarchy, with each website listed separately, and you could either allow or temporarily allow entries. A deeper system menu allowed a more fine-grained control, including whitelisting, specific element blocks, and more.
NSS 10 comes with a matrix-like grid, similar to the uMatrix extension, which we will cover separately. Sites are listed on separate lines, and there are currently five buttons next to domain names. If you click on any one of them, you will toggle the specific scope for the particular domain, and also be able to see details.


Scopes
The scopes are as follows:
Default - by default any site that is not covered in any other scope, will be matched to this one. The eight available element categories will be toggled on/off. The default is to allow script, object, media, frame, fetch, and other. Font and webgl are not allowed.
Do note, the default is to actually ALLOW scripts.
So this is one major difference compared to Noscript 5.x, and this is something that you can and should change. I will show you how to achieve this shortly. Please bear with me.
Trusted allows everything for the listed site.
Conversely, Untrusted does not allow any element for the listed site.
Custom is the fourth category, and it lets toggle the state of any one of the eight elements for the particular domain.
The padlock symbol allows you to match the rules in the four scopes earlier either to websites that are served through the secure tunnel (SSL/TLS) or any (HTTP). This means that if you go to https:// versus http:// version of the same domain, should they exist, the behavior may be different.
How does this work?
Well, this works completely opposite to the 5.x series. There, permissions were per-site. Here, because of the different architectural format of the data stored in the backend, the permissions are per scope, and sites are included in each.
Noscript 5.x - site, permissions
Noscript 10.x - scope, permissions, site, override permissions
This is confusing, because if you change defaults for a particular site, it will actually change the defaults for the ENTIRE scope. This is broken by design, and it should ideally be altered soon.
You can test by going to a domain - say dedoimedo.com, and then make a custom rule for it, which allows scripts. If you go to another site, you will learn that the same rules will be applied, because your edits affect the entire scope.
Temporarily allow
The remedy to this issue SHOULD be the use of the temporarily allow option, which does exist. Under Custom, there's a small clock like button. Once you select the desired toggle state for the eight elements, click this button. This should make the permissions temporary, and they should revert back to the original once you close and reopen the browser.

Notice the clock icon to the right of text that reads CUSTOM.
Unfortunately, at the moment, it seems that the temp-allow mode does not work. Whether you click the clock button first and then set the permissions or set them and then hit the button, upon browser restart, your changes will have become permanent for the entire custom scope. This seems to be a bug and it needs to be fixed.
Temporarily allow, option 2 (update)
A fellow named Krusty suggested the following model to temporarily allow sites. Instead of using the custom scope, use the TRUSTED scope, and then click the small clock icon to temporarily allow, without messing with the specific elements. You can manually reload or close the overview window, and the page will reload automatically. This works for two out of three cases for me, as in the temporary permissions are gone after you restart the browser, so that is already some progress in the right direction. Thanks, Krusty.

Options & JSON configuration
If you open the options/preferences menu, you have a relatively limited set of tweaks at your disposal. If you have migrated from 5.x, you should have all your whitelisted sites there. The UI allows you to toggle the state of each, but not to delete them. Here you can change their default state among the four scopes, or completely remove them from the list.


Debug
At the bottom, there's a debug button. Select it, and this will open a small text editor, inside which you can change the JSON configuration for Noscript. You can edit the default state of each scope as well as delete whitelisted entries. For instance:
{
"DEFAULT": {
"capabilities": [
"frame",
"other",
"fetch",
"media",
"object"
]
},
"TRUSTED": {
"capabilities": [
"script",
"object",
"media",
"frame",
"font",
"webgl",
"fetch",
"other"
]
},
Above, I have deleted the "script", line from the DEFAULT scope. You can also do that through the UI. When you select any which domain, untick the script box, and this will apply for all websites that are marked with the DEFAULT scope option. Not intuitive, I know. Likewise, domain entries:
"sites": {
"trusted": [
"§:addons.mozilla.org",
"§:afx.ms",
"§:ajax.aspnetcdn.com",
"§:ajax.googleapis.com",
"§:bootstrapcdn.com",
"§:code.jquery.com",
If you don't want to trust some of these, just delete them. As you can see below, the UNTRUSTED scope does not have any elements (capabilities), nor sites at the moment, and custom is also empty.
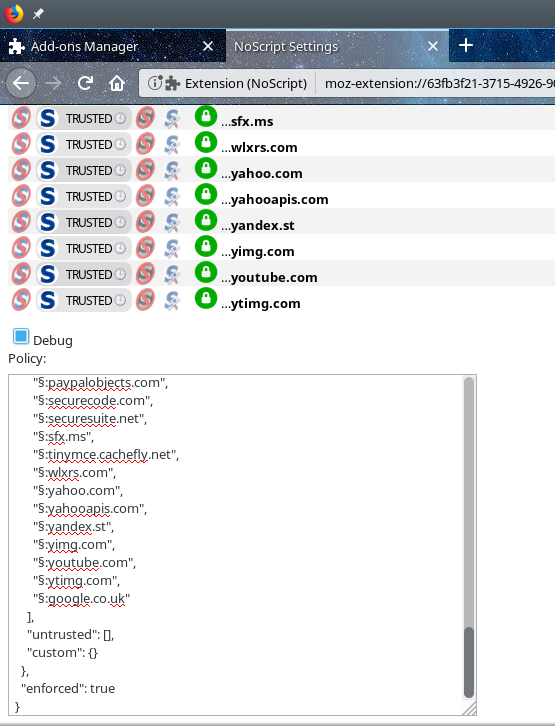
And here's a sanitized list of sites:

Working with Noscript 10 & suggestions
At the moment, this is quite cumbersome, I must say. Toggling site states takes much longer than the simple middle-click that Noscript 5.x has. This should be reintroduced as a feature. Moreover, since you affect entire scopes and not just sites, the permissions changes become largely useless. The temp-allow does not work at the moment.
You do get automatic reload of websites, but overall, the flow is much less streamlined than it was. I believe this ought to change as new versions of Noscript are released. I think Giorgio Maone should introduce multiple configuration files for each scope, and also keep configurations in the following format:
{
"DOMAIN": {
"capabilities": [
"frame",
"other",
"fetch",
"media",
"object"
]
},
Whatever isn't matched, is then associated with DEFAULT (whatever it is). Temp-allow would skip the domain names and use a new scope called TEMP-ALLOW, which is erased on every browser restart (or manual change).

Of course, there are also aesthetic considerations. The UI should have bigger text and more spacing between elements. Each domain should have give toggles - between the existing scopes and a NEW scope called temp allow. There should also be a global button to allow all. Configuration of the scopes should be done in the main options window.
Conclusion
Noscript 10 was probably rushed too early, in order to meet the Firefox Quantum release schedule. It does not feel like a complete product, and it highlights the mess that the WebExtensions idea really is. I am confident that Noscript will evolve and change and improve, and that it will match the old behavior, in function if not the look.
The most important things at the moment are to be able to use temporarily allow function for all sites, and not to affect scope settings with per-site tweaks. The hierarchy of the JSON should be therefore driven by the smallest granularity component, and this is the domain you're visiting. Well, that would be all for the first guide. If you have any questions, please ask, I'll add the answers here. Updates and news coming soon, so please stay tuned for the 2nd edition, and whatever else is relevant on this topic.
Update - November 23, 2017:
Well, before I write the second edition of this guide, I felt it is more prudent to add some rather important updates to this page. Just a day after I've published my article, Giorgio Maone has updated the Noscript extension, and it is already looking much more streamlined and efficient.

The new and redesigned UI still keeps the four categories, but most importantly, it gains the temporary allow button, the ability to revoke temporary permissions, and a separate icon to open the settings. Apart from an extra click - Noscript 5.x let you temp-allow all via middle click on the extension icon - the behavior seems to be largely the same as in previous versions. There are still some fine nuances, but it is the add-on that we love, care and need to warrant using Firefox. This is a great development. Stay tuned for more.
Cheers.