Updated: July 30, 2008
Whether you should or should not use a router at home is a question open to debate. The answer relies on your needs as much as on your setup. A single computer user will be less pressed into trying a router than one running a small farm of PCs. Regardless of the outcome, there is one undeniable advantage that the router offers: network modularity.
It allows you to separate the network access control from the operating system, whatever it may be. Since the packets flowing through the cables are identical for Windows, Linux, Mac, and pretty much any other operating system you'll find in a home environment, the router makes a logical choice of making sure the network is up and available, no matter what you're running on your machine. If you're a Linux user, the prospect of modularity will definitely appeal to you, as the entire concept of the Linux operating system (as a whole) is modularity, which leads to stability and simplicity. In practical terms, this means that configuring a home network becomes a very easy and painless task.
Furthermore, the router allows you to keep the network grid rather simple: each machine sees only the router, which is responsible for the more complex processing, like IP forwarding, port forwarding, share access etc. Last but not the least, the router can be a very effective firewall device. For Windows users dreading hacker attackers day and night, the idea of an impregnable forward defense layer may sound rather promising. Taking into account that most routers run a minimalistic Linux kernel that has very few vectors of exposure, plus the fact you won't have to bother with complex software firewalls that slow down the system, using a router becomes a very lucrative investment.
So, assuming you do like the prospects of a router device and have decided to purchase one, there are some security consideration that you should take into account when setting up.
Security setup
There are many, many guides telling you what you should do with your router ... and here's another one! Seriously, I think I'm going to give you a slightly different perspective on router security. My hope is to help you understand the fundamentals of the router (security) functionality, so that you can use its functions wisely. Just remember that you need not follow the rules blindly. Make sure they fit your needs and skills.
Administrator password
This is the very first thing you should do. All routers have a graphical control panel through which its various functions and settings can be modified. The control panel can be accessed only through a wired connection and by authentication with username and password.
Using the default, factory-set password may allow a potential villain to access and change your router settings without your permission. Therefore, it's wise to alter the password the moment you start working with your device. You should use a strong password, containing alpha-numeric characters.
Firewall
One of the most important strong sides of router devices is that they can function as firewalls. Unsolicited inbound connections will be refused. If the router is configured to drop the packets, you will get a so-called 'stealth' result in online port scan results; if the router is configured to reject the packets, the ports will be closed. Either way, you'll have a robust entry-point control. Therefore, you should keep the firewall enabled.
See sample image:
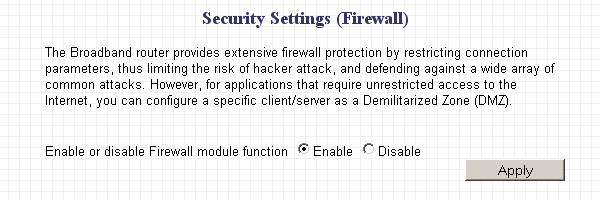
Advanced settings
This is not a necessity, mainly a bonus. If you are only interested in general practice, without too many technical details, simply skip this sub-section.
Many firewalls also feature 'advanced' options, some of which can be used as a security measure. One of these features is the ability to block ping. All in all, this is a good idea, but you should not block ALL pings. You should allow your internal network computers to be able to ping the router. This will allow users on your computers to know whether the router is up or down or reachable should a networking / connectivity problem occur.
Therefore, you should allow some ping - again, only for your internal network:
- You should allow incoming ICMP Type 8 (Echo Request) from your internal network.
- You should allow outgoing ICMP Type 0 (Echo Reply) to computers on your internal network.
- You should allow outgoing ICMP Type 3 (Destination Unreachable) to computers on your internal network.
If the clients on the internal (local) network are also using firewalls of their own, whether inbound and possibly also outbound, then similar rules need to be setup for each one of them. This is an advanced topic on networking and firewalls, thus it won't be discussed here. But it's something you should keep in mind if you aim for a tightly controlled setup.
Port forwarding
For most people, the router experience will be a transparent process. They will rarely have to interact with this curious little device. However, users of Peer-to-Peer (P2P) networks and gamers will most likely not be able to use their favorite programs and games out of the box.
This is because most of the P2P client programs and online games require server rights to function properly. In other words, they require inbound connections to certain ports. But the router firewall will not allow inbound connections. That is, unless port forwarding is enabled.
This fancy terms means simply allowing unsolicited incoming connections to certain ports, namely those of the relevant programs and games.
Therefore, to make your software work, you will have to open a number of ports in the firewall. Please note that this invalidates the firewall function for those specific ports, making all and any applications installed on the computers behind the router and bound to these ports accessible to the outside world.
You should use port forwarding with caution and care. Do not be tempted to turn the firewall off or enable a wide range of ports just because your programs do not work. Most applications use only a very small number of ports. If you do not know what they are, browsing through a manual or Googling online will yield the desired answers. With just a bit of patience, you should be able to setup your programs within minutes.
Here's an example:

Universal Plug 'n' Play (UPnP)
This fancy name refers to routers' ability to dynamically open ports for applications that require them. On one hand, this allows for a certain level of flexibility, especially for clueless users that do not wish to tamper with manual port forwarding. On the other hand, it could be a security breach.
Recently, there has been a lot of talk about router being vulnerable to javascript exploits via browsers, enabling possibly 'rogue' websites to alter router settings. The similar principle applies to installed applications.
While all these threats can be mitigated by: a) using a good and secure browser b) using a good and secure browser with javascript control (like Noscript in Firefox) c) making sure your machine is not infected, it is still wise to disable UPnP to prevent 'accidents.' This will force you to use manual port forwarding, but it is safer and gives you more control over your network. And it's quite simple actually.
Wireless
Many routers are also capable of supporting wireless devices, for example laptops. The security implication of such a setup is that wireless router and the respective devices must send radio signals to one another. These signals can be intercepted by anyone with the right equipment, allowing them to easily track your wireless communications. Just for reference, sniffing land lines is also possible, but it is more difficult because cables are usually laid underground and heavily shielded.
This means that you should use encryption to scramble your communications so that any 3rd party listener will only be able to capture encrypted noise and never see your true data.
Furthermore, the encryption also serves to authenticate users. In other words, providing the right credentials will allow users of wireless devices to both connect to your network and properly decode its communications.
Therefore, no one will be able to sniff your traffic. And no one will be able to use your network without your approval. The leechers could also possibly implicate you in embarrassment or even legal issues by doing mischief or crime while happily logged to your IP.
Encryption & password
Different brands of routers offer different encryption methods. You should always go for the most advanced, most difficult-to-break method. Today, WPA2 provides the most secure encryption method. WPA is also OK. WEP is the oldest and least secure method - but it is still better than nothing. Use any one of these, the stronger the better.
There are other subtle variations and possibilities to these three encryption methods, but they depend on the router brand and your needs - and go slightly beyond the scope of this article. If necessary, I'll address them in a follow-up article should a popular demand arise - or in email queries, should you send them. The most important thing to remember is to use encryption. Use WPA2, if available, WPA next, WEP last.
Either way, you should you a strong password. For one, it should be different from the administrator password used to access the router control panel. For two, it should contain alphanumeric characters and be long. How long is open to debate. Some people suggest 64-bit passphrases, but this might be going over the top. A reasonable password 8-12 characters long is quite sufficient for realistic scenarios, especially at home. But it's your choice.

Service Set Identifier (SSID)
This parameter specifies the name that your router will use to announce itself to other wireless devices seeking to connect to it. You should change it to something reasonable so that you know which network you're connecting to - and also 'warn' others that this is not their network. A presence of several 'default' routers might confuse everyone in the neighborhood.
Security wise, this is not a critical feature, but you should be aware of it. However, it does have some merits. It might turn off potential villains from trying to probe your network - the fact you have change the SSID might be an indication that you are security conscious and have probably changed the default settings, and thus, not worth the bother. The alternative name also disguises your router brand, making it more difficult to attack.
And no less importantly, please remember NOT to use any personal information in your router name! You should go with funny nicks that you have always liked as a child - something like Zagor, ElmerFudd etc.
SSID broadcast
Unlike most guides, I do not recommend disabling this feature off. It will merely inconvenience you without providing you with any extra security. Those who want to find you - will. The last sentence does not mean you will be swept in a hacker tornado. It merely tells that burying your head in the sand will not really make you invisible. At most, it will prevent annoying neighbors' kids from trying to connect to your wireless network - and giving up after providing incorrect password once or twice.
Other settings
Demilitarized Zone (DMZ)
This vigorous term means a very simple thing: allow one or more of your computers, printers or other network-aware devices to be without the firewall protection of the router device. In other words, this allows you to selectively protect your array of machines with the router firewall.
Devices placed in the DMZ will be 'exposed' to the Internet, which may be something you want. For example, this could be a test machine, a server, a web camera, or any other device that you feel should have unhindered access to the web - and vice versa.
My suggestion is to use the DMZ sparingly, just like port forwarding. At the very least, you should make sure you understand the potential implications of your actions - and make sure that exposed devices are patched with the latest software / firmware upgrades. This way, even though they might be a tempting target to e-villains, they will be less likely to succumb to potential attacks.
In fact, here's a general recipe; before 'loosening' your router security, always try doing things the simple way:
- First, try to get your devices or applications to work without making any changes.
- If this does not help, try enabling port-forwarding for that particular application.
- Only if both these failed, try placing the device in the DMZ.
MAC filtering
You may have heard this one, too. Each network device has a sort of a fingerprint - a unique hardware address that identifies it. This hardware address is used in network communication between devices, mainly to tell one another who they are and what IP address they're using.
Routers can be configured to allow only devices with specific hardware addresses to access the network, both wired and wireless. This could be considered a security advantage - but it is not.
Hardware addresses can be spoofed rather easily, making any blacklist/whitelist filtering based on this parameter rather tricky to enforce. It is also somewhat redundant. There's very little chance that someone might sneak another computer into your network - this might happen in a large corporation with hundreds of computers, but any home user will definitely spot the 'extra' PC suddenly appearing on his desk. For wireless devices, this may be a sound advice, but it's a secondary issue if your wireless access point - as it should - is protected by a strong password.
To sum it, should a 'hacker' get past your wireless encryption and get to use your wireless network with wild abandon, you should be worried about the cracked password than spoofed MAC addresses.
Static IP addresses
Static IP addresses are not exactly a security matter. However, if you have quite a few computers on your LAN, it is a wise idea to configure static IP leases for each one, so that your setup remains static - and thus predictable and to avoid any sudden conflicts due to possible changes.
Please note that you should not change anything on LAN machines. Leave their network configuration set to default, which is probably automatic IP configuration via DHCP server - in this case the router.
Through the router interface, you will have to assign static IP addresses to each computer, or more accurately each network interface. These interfaces will be identified by their MAC address. Thus, you will create static pairings between IP addresses and MAC addresses. This grants you greater control over your network and can prevent annoying setup bugs.
Firmware upgrades
From time to time, your vendor might issue an upgrade / patch for your router. If this release is meant to plug a security vulnerability that might be remotely exploited, you should apply the patch. Please note that this may cause your router to cease function, ruin your configuration or just generally mess things up. Therefore, you should be careful when applying patches. And most importantly, back things up!
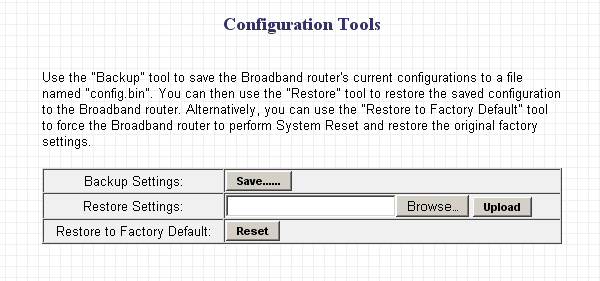
Backups
Your router may have an option to reset the configuration to factory settings. It should also have the option to backup the configuration file. You should do this before making any significant changes. You should do this once the moment you 'install' the router - i.e. backup the default configuration - and once after you've set everything up. This will also help you more easily get back on track, should a router firmware upgrade fail and/or should the actual device die and you buy a new one of the same type.
Conclusion
My recipe for router security is probably more lenient than most guides you have seen and read. This is because I stick to practicality rather than paranoia. The chances the 'evil hacker' lives in your neighborhood and wants to crack your wireless network are not that big. Most likely, you are surrounded by people just like you, who just want to enjoy their electronic toys without too much fuss.
Then, there's the issue of probability. How likely are you to get hit by intrusion attacks? Your home is not a public access point at an international airport.
Personal experience: in the last year or so since I've been using a router in one of my setup, there have been precisely zero attempts at trying to connect to my network. This includes a happily broadcast SSID and no MAC filtering.
So, to sum it up: Change the administrator password; use a strong password. Use the built-in firewall. Use port forwarding sparingly to enable server rights to specific applications (like games, P2P programs). Do not use UPnP to dynamically open ports; use manual port forwarding instead (see above). Use encryption for your wireless network; you should use the newer, more advanced encryption methods if possible; the preferred order is like this: WPA2, WPA, WEP. Use a strong password for your wireless network; use a different password from the administrator one. Change the default SSID name; there's no urgent need to disable SSID broadcast. Use DMZ with care; you should try default settings and port-forwarding first. MAC filtering is not necessary, you may use it if you want. Static IP addresses allow you a more finely tuned control of your network. Consider upgrading your router firmware if the vendor issues a patch, especially if it addresses a security vulnerability that might be remotely exploited. Backup your router configurations before making any major changes, especially a firmware upgrade. That's about it. Have fun. If you have questions, feel free to contact me. I'll add the more common questions - as well as the answers - as an appendix to this article.
Cheers.