Updated: July 11, 2018
Windows 10 disables SMBv1. Windows 10 does not disable SMBv1. Windows 10 may disable SMBv1. I've been seeing a storm of these claims recently, revolving around Windows 10 Builds 1709 and 1804, which state that Microsoft has removed the SMBv1 protocol from Windows. This means that users trying to connect to other boxes in their network (most likely home environment) will not be able to do so. Maybe.
In my review of Build 1804, I did not encounter such a problem, but then, this was not a fresh install, and I was using a well-configured, existing setup. So I decided to perform a full, fresh, clean install of Windows 10 and see what kind of behavior awaits me. This should also put to rest all the rumors and counter-rumors.
Setup
First, I downloaded the Windows 10 ISO file. Then, I configured a virtual machine setup. I installed Windows 10 from scratch, and purposefully selected Home edition, because Pro is always easier to use and configure due to Group Policies and whatnot. Next, I configured an offline account (meaning local, meaning no online nonsense).
Once I reached the desktop, the very first thing I did was try to access one of the hosts in my LAN. I did not tweak any setting in the desktop, played with either Windows Defender or firewall rules, or anything alike. The only thing worth mentioning is that I used a bridged network adapter so the virtual machine gets assigned a new IP address in the same range as other household devices on this network, e.g. 192.168.1.106 or 192.168.1.109.
I launched the Windows Explorer and in the address bar typed: \\<hostname>, something like \\dedoimedo. I reached the other Windows host (Windows 7 that does not have SMBv2 or SMBv3) without any problems. The sharing works just fine and there were no issues.
Windows Features
I also heard claims - and received a dozen emails where people claimed that not only is SMBv1 disabled, you cannot reinstall it. Perhaps they have encountered some bizarre scenarios, but I am unable to replicate those. Under Windows Features, you have SMBv1, and you can add/remove it. This is in line with the official documentation - not that it can't change sometime in the future. However, I don't see a problem.
However, please do note - Windows Features also includes Automatic Removal entry for the protocol. If you do not use Samba sharing within 15 days of the installation (excluding powered off time), the SMBv1 protocol will be disabled. You can untick this box, and SMBv1 will NOT be disabled even if not used, and of course, if it is, it will not. And even if it's gone, you can select the second checkbox and install it. The same as Telnet and TFTP and other protocols that have long, long been disabled, for supposedly similar security considerations.
Telnet is an excellent example. It was disabled even in Windows XP by default! Still, if you needed it, you could always turn it on, like any other Windows feature, either using the GUI below or through the very nifty and powerful dism /online /Enable-Feature /FeatureName:<feature> from the command line. This is because some legacy applications may require this, and Microsoft offers very good and robust backward compatibility, and this is one of the reasons why it is so popular in the business world.
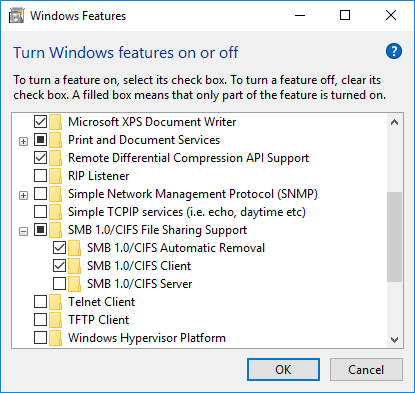
Network discovery
Now, this is something that may throw people off. In Windows 7/8, you would get the HomeGroup greeting whenever you connected to a network, and it would ask you to classify the network - private (trusted), public (untrusted) and work (semi-trusted). Windows 10 dispenses with the HomeGroup concept, and it does not ask you to classify your network.
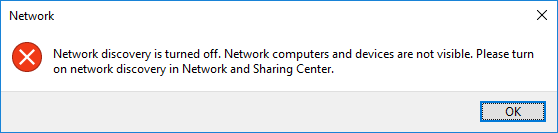
In my case, for this installation - and I presume for most people - the network was set as Public - and this means that network discovery and file and printer sharing are disabled. This means you can't browse networks, but you can directly connect to devices (as I've shown you above). You can either change the network type through the Settings, change firewall rules, or allow certain types of content for public networks. For example, I enabled network discovery but no file sharing. And indeed, now Windows 10 shows certain network devices just fine, including computers and printers and whatnot.
Conclusion
Whatever you think about security nonsense like this whole SMBv1 scaremongering, it would appear, with a very high degree of confidence that a) SMBv1 protocol works and even if it's disabled you can enable it again through Windows Features b) you can directly access network devices, and you may need to change your network type and/or specific sharing/discovery settings before you can browse the network. Windows Defender did not interfere with my attempts to access the Samba shares, and I had the expected functionality.
My test shows that we have the freedom and flexibility we need. I detest the whole security drama, I find all this new-age online integration moronic and useless, but I also hate when people spread baseless fear. Much like Linux, where you can change the client protocol to use Samba, Windows 10 Home - and Pro is an even easier game - does give you the necessary tools to control and manage the use of SMBv1. Like I said before, this could change, but for now, I do not see the doom and gloom.
Hopefully, this article was of use - it highlights what happens in Windows 10 after a clean install, how to access network devices and shares directly and indirectly, how to disable/enable Windows features, how to change your network profile and/or selectively configure network discovery and sharing, and a few other tricks. This should remain relevant at least until 2020, as Windows 7 accounts still for almost half of all Windows installations, and there are countless other appliances that use SMBv1. There you go.
Cheers.