Updated: March 13, 2009
I usually refrain from writing malware-related articles as I find it rather difficult and quite futile to try to keep with the pace of carelessness and disregard that most people exhibit for their computers, but I decided to make an exception and spill a word or two on the subject.
First, don't panic. It's just another in a long series of advisories. It happens to concern PDF software this time, that's all. Second, as always, using your head goes a long way, especially if you have a big head. Let us talk about what you should do when faced with a possible PDF threat.
Rule 1: Don't open/download suspicious files
Files are like dogs. If you don't provoke them, they won't bite you. If you do not double click them, they will not execute. It's the golden rule of execution. No run, no fun. The problem begins with the decision to download a file. Not sure? Do not download it. This has always been true regarding suspicious payload, whether it comes as an attachment to an email, a download link on a website, a file on a friend's USB drive, or any other method.
Wait! The recent exploits also work without opening the file!
Yes, so the rumor goes. The particular issue is only relevant to Adobe Reader and the way it interacts with Windows Explorer. You may want to read this article for many more technical details.
Windows Explorer can potentially execute malicious code by reading file information. This brings us back to point no.1. Do not download suspicious files. Thus, Windows Explorer will have nothing to execute.
Rule 2: Patch your system
This is a good idea, in general. If your system/programs are patched, the vulnerabilities are closed and potential risks mitigated. The simplest course of action for most people is to install vendor patches and continue their happy, careless computer usage.
Rule 3: Use alternative applications
Some may call this idea security through obscurity - evade common problems by using uncommon programs. This is partially true. However, there's another reason not to use Adobe Reader as your default PDF program. It's a big, heavy application, worth 200MB of code. In comparison, a fairly popular, lightweight alternative called Foxit Reader weighs only about 2MB. Statistically speaking, this means that Foxit Reader has approx. 100 times less bugs than Adobe Reader. According to Secunia, this is pretty much true. Less code, less complexity, less bugs. So you should definitely consider other programs.
But Foxit Reader is vulnerable, too!
In the words of Sir Humphrey from Yes (Prime) Minister, the answer is: yes and no. The program does have a vulnerability. And it concerns the way Foxit Reader handles images in the jbig2 format. All right, but wait a second ...
Since I'm using Foxit as my favorite Windows PDF reader, I decided to heed the security advisories and patch my copies of Foxit Reader. So I launched the update facility and here's what I got:
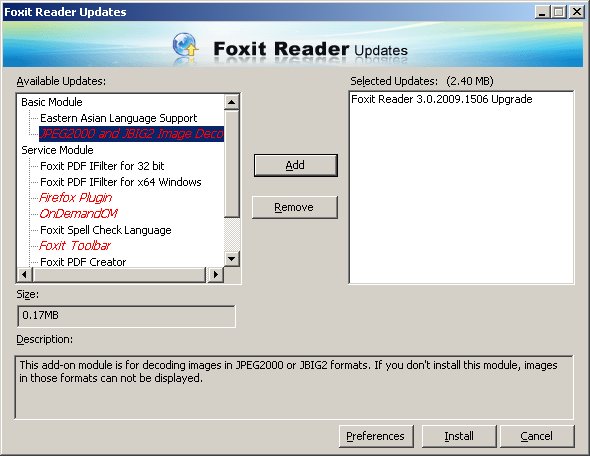
As you can, there's an update available, which I've already placed in the right pane. On the left side, the available modules include a JPEG2000 and JBIG2 Image Decoder. The description field informs me that if I do not install this module, images in those formats cannot be displayed.
So, we have an update to address a vulnerability in the way the application certain formats, which, in my case - and which happens to be the default install of Foxit Reader - are not supported in the first place!
What am I trying to say? First, listen to what "experts" have to say, but do use discretion and a bit of cool-headed judgment. Security companies are like news agencies. They love to frighten the common man into submission, obedience and docility by bombarding him with terrible doomsday scenarios, which happen to increase ratings, income, popularity, and control. Think before doing things, including managing your system resources and needs.
In this case, Foxit Reader may also be a target, but there's a patch available. There are other programs available, as well, which are not vulnerable to the issue at hand. We will talk about PDF software in a dedicated article, including readers, distillers, converters, and more.
Rule 4: Harden your system
Even if you stick with Adobe Reader, you can make it less vulnerable to potential problems. This can be done by disabling potentially unsafe functionalities and preventing buffer overflows.
If you want to learn more about buffer overflows, take a look at the Wikipedia article. In general, buffer overflows are situations where an application runs code beyond the allocated space in the system memory. In other words, it runs something the something did not account for, which could be malicious code.
Use Data Execution Prevention (DEP)
I wanted to write a separate article on DEP, but decided on presenting the subject in this article. Windows XP and its successors have a handy feature of being able to restrict applications from misbehaving.
Turning on DEP for potentially troublesome programs will prevent them from using memory beyond the allocated range. If they do so, they will crash rather than cause damage to the system. In Windows XP, you can access the DEP setup via right-click on My Computer > Advanced > DEP.

DEP is not a perfect solution to a bug-free, smooth-running environment, as some programs do not like it and will constantly crash, but it can surely help.
Disable Javascript in PDF readers
Some PDF readers can parse Javascript code. This turns them from basic readers into rich applications, which can interact with users via forms, buttons, etc. A bad idea altogether, in my not so humble opinion, but it's the way things are and we should try to handle them the best we can. Optimal course of action: disable Javascript! Here's how you do it in Adobe Reader:

Rule 5: The principle of least privilege
Most Windows users run their operating system as administrators. This is not bad, but it can be better. It's possible to significantly reduce exposure vectors to threats by running a limited account, similar to what is normally practiced on UNIX-based operating systems. The basic idea is: if applications do not have system privileges, they can do far less damage.
In Windows XP, you may want to use SuRun, an extremely elegant and friendly program that converts your user to a limited one, while allowing you to conveniently escalate your privileges when needed, like software installations, for instance.

Rule 6: Use Linux
The recent vulnerabilities were reported for all operating systems, but the truth is, most of the talk was about what happens on Windows. Linux was not really mentioned, except to spice up the story.
Vulnerabilities may indeed be present on various PDF readers on Linux; that's one thing. Exploiting them is another. Due to its robust configuration, with users running with limited, non-system privileges, Linux is far less susceptible to these kinds of problems. Additionally, having a centralized, automated software management system means that even if there are vulnerabilities reported, they will be patched very soon, if not already.
Conclusion
The world is not going to end any time soon. Problems with software have always existed and will continue to exist. As a user, you can exercise some healthy thinking and gracefully evade trouble hotspots and difficult situations that may compromise your systems or data.
The above rules are more sort of guidelines, but they should serve you well. Likewise, you may want to read my Safe Web practices article, which details some common tips and tricks that should help you weather the storms of the wild and choppy Internet.
Have fun.