Updated: July 3, 2019
You all know I'm a sucker for smart, intelligent software. And by that I mean tools that are designed correctly on a philosophical level; they solve strategic problems rather than tactical annoyances. In Windows, two prime examples of such design are EMET and Exploit Mitigation, fire-and-forget security concepts that don't use the outdated blacklist model of filtering out bad software. Instead, they use a philosophical approach of filtering out illegal memory instructions. It doesn't matter what your app is, if it behaves badly, it goes down.
This means I was quite intrigued and almost ended up being keen after reading about a recently unveiled Microsoft software solution called Windows Defender Application Guard, which uses hardware isolation to block threats. Sounds like my kind of tool. No signatures, no chasing one's tail. Instead you get isolated browsing instances, and whatever happens inside them, stays inside them. Like Las Vegas. So I started testing.
Application Guard setup
And had my hopes dashed right away. Application Guard is designed for enterprises, well much like the other two security solutions, and so it requires at least Windows 10 Pro, unlike the other two solutions, and that's something I didn't have on my test machine. I knew my attempt was going to fail. But I wanted to complete my testing session and write this article, because there are important lessons to be learned here regardless. So while we shan't be having a happy moment at the end of this piece, you will not have just read another useless piece of Internet fluff.
There is an element of somewhat shameless self promotion, of course (not me). Application Guard uses Microsoft Edge as the underlying isolation engine (with Hyper-V in the background). To that end, it is offered through a browser extension for both Firefox and Chrome. Yes, you read it right. You install extensions that let you launch isolated tabs using Edge. Back in the day, you had IETab for Firefox. Well, similar, except the underlying technology is different, and the focus is on security rather than compatibility.
I started by installing the Firefox extension. This opened a tab that informed me I needed another step, and that was to get the actual Application Guard, eh, app from the Store. I found this to be an incredibly badly orchestrated idea, for many reasons.
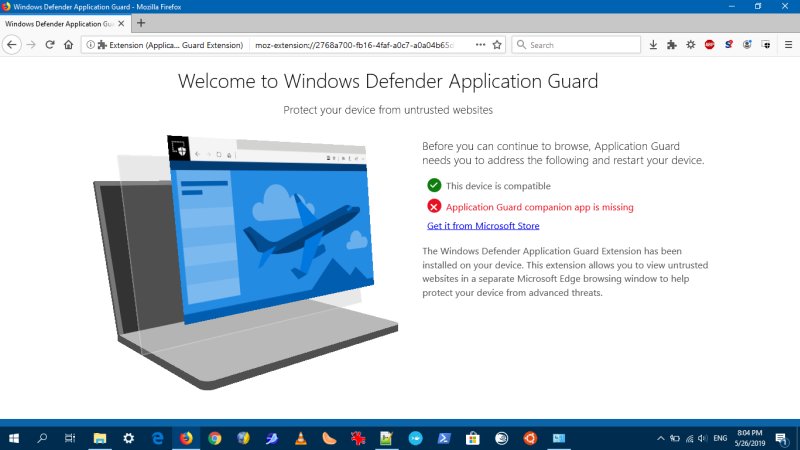
One, If I'm not mistaken, Windows Enterprise typically does not use the Store. Two, with the unfortunate demise of the Windows Phone, the whole store idea is sort of pointless, so pointing [sic] people there doesn't really have any value. Three, you need to install the App Guard component through Control Panel - still more valuable and useful than Settings four years later. Four, back to the Store, it will of course nudge you and prompt you to use an online account, but if you're using a local setup - or enterprise logon - then this completely misses the mark.
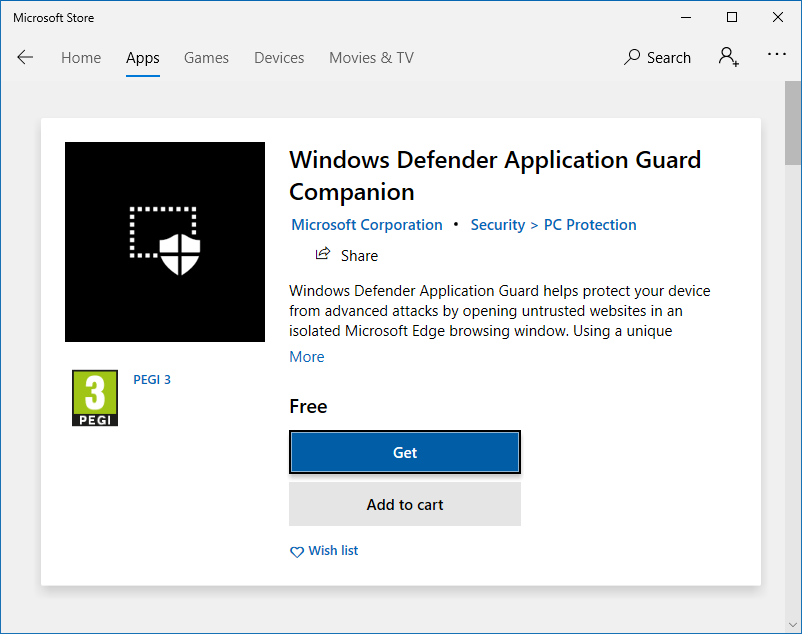
At this point, I also happened to test my operational setup - as I've changed the store and WU settings, and with the services disabled, Windows couldn't install the companion app. But I turned these services back on, installed the app, and then turned them off. Easy peasy.
However, while I was doing the setup of the app - Firefox browsing was blocked! Yup, the App Guard extension was preventing Internet connectivity. Again, this is bad design. Because it forces users to complete the setup right away, and they don't necessarily have access to the Web to search for answers or information they may have while doing this.
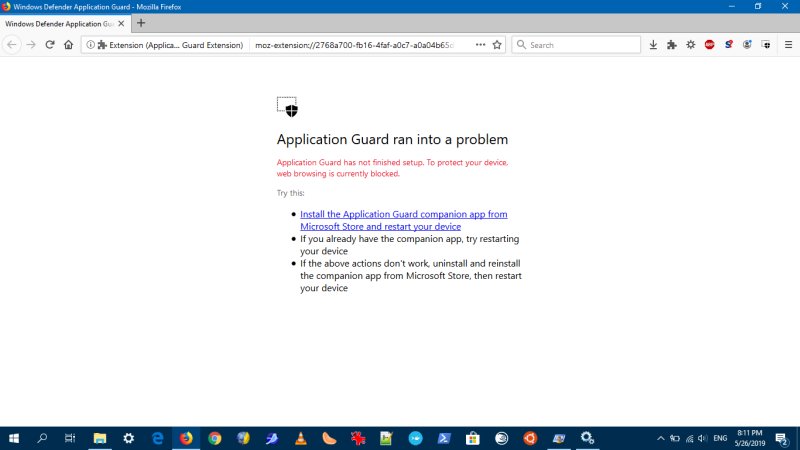
You can work around this by disabling the App Guard extension, but really. There are so many ways, elegant ways this could have been done. For instance, offer everything as one bundle rather than scatter the setup across four different vectors. Or maybe not feed the setup piecemeal.
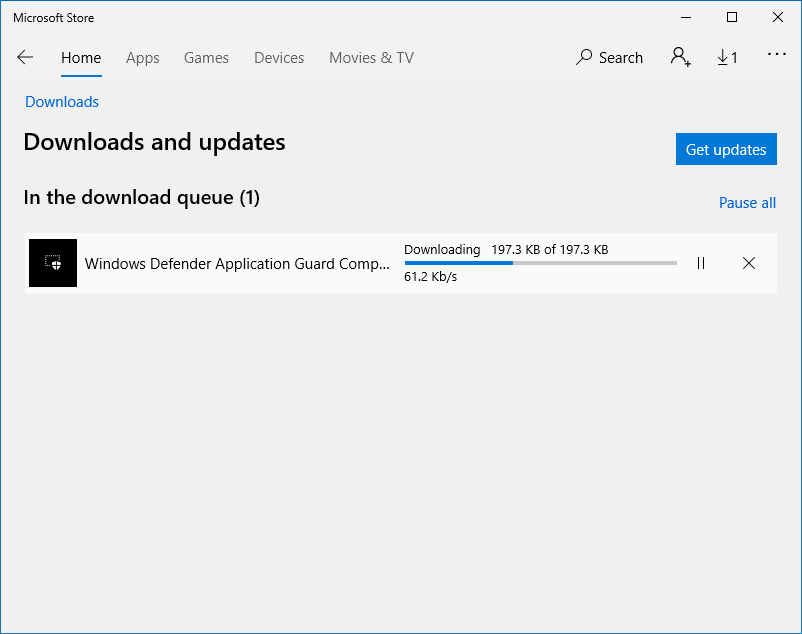
Once this step was complete, the Firefox extension screen now showed another missing piece! And this was the one I could not fix - Home edition and all that. But then, why wasn't this shown right away? This way, it feels the whole effort was there to make me go to the Store and install an app.
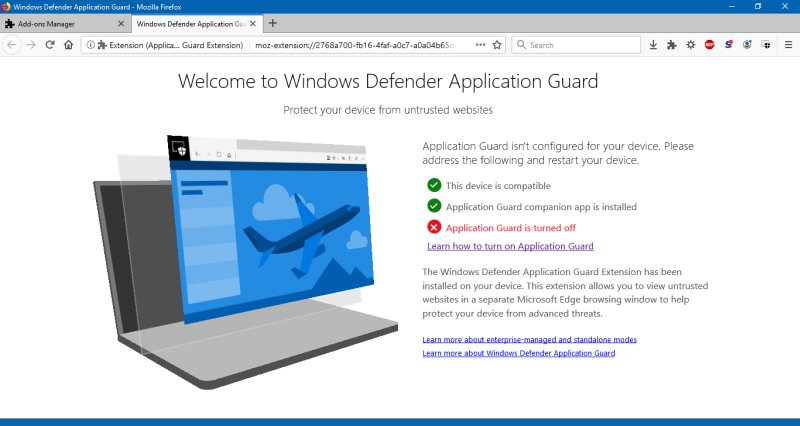
I was really annoyed. There was no reason to have me install the companion app if the system is Home and cannot use the technology. But I guess Microsoft is repeating the same mistakes all over. We had the aggressive marketing with GWX, we had it with forced updates, and now this. Not professional.
After all, if this software is intended for serious people, they will not be monkeying about the Store, they will surely not be using it as it's pretty much a dead platform - woe my Lumia 950 right, right! - there's also a pretty good chance they will be using a local account, and in the enterprise, a whole different set of rules applies.
Microsoft could have offered a single MSI or EXE that does everything - add the optional Windows features like Hyper-V and Application Guard, configure the system - and only leave the extension configuration to the browser users. That's it. But apparently, there was a checkbox that had to be checked somewhere, and it read Store. Then, reading the fine print, there's also the mention of diagnostic data. Sigh. Will they never learn?
And then, there's actual configuration, if you get everything running.
Security benefits
I will reserve my judgment for until and when I do test Application Guard - you might want to read the ghacks article on the topic, as it sheds a wee more light than my sad-face attempt. But I have a whole bunch of questions. If it's made with the same kind of sensible philosophy like EMET and Exploit Mitigation, then it will be a supreme product. But then ... First, Edge now uses the same engine as Chrome, so the concepts of security and sandboxing are similar. What's the added benefit of Application Guard in this instance?
How does Application Guard fit alongside Exploit Mitigation? I mean, I have mitigations enabled for various programs, but NOT for Edge, because I don't use it. Does this mean my exploit-hardened Firefox has better security than the non-hardened Edge, regardless of the actual browser baseline security?
Speaking of Firefox, if you use Adblock and/or Noscript, there's a good chance you're filtering out a lot of noise and garbage, which also coincidentally happens to be associated with security risks. What additional benefits does Application Guard introduce that aren't covered by the above?
The most important question ...
Home edition users don't get this nice thing. But then, if it's really good - based on what I was able to read, no actual testing just yet, then it begs the following question:
If Application Guard is so important and effective, why are Home edition users being left unprotected? And if Home edition users have adequate security already, then is there real practical value to Application Guard?
Conclusion
Application Guard sounds like a really cool thing. But the current implementation is rough. First, Home edition users are left out, but okay, I get it. The setup is clunky. There's no reason for piecemeal checkbox exercise in the browser extension screen - if the system is not compatible, the Store step is unnecessary. And it is unnecessary regardless. Because this is not a viable delivery method in the post-mobile Microsoft era, and it simply does not align well with typical Pro or Enterprise modes of usage. Then, there are practical questions on security, and the value of Edge as the browser used in the isolated environment.
I can't escape the feeling this is more than a great security feature. It looks like an attempt to make people use Edge, one way or another, after roughly fifteen years of steady market share decline in Microsoft browsers. The overall container + isolation idea is quite interesting. It's fresh, it's innovative, my kind of fun. But then, does it solve the real problem, and that is people doing silly things with their browsers? And then, are so-called drive-by exploits a thing in modern Firefox or Chrome? I don't know, maybe.
One day, I hope to have practical answers. If Application Guard is anywhere as robust and flexible as EMET and friends, then it might be a worthy tool, browser engine notwithstanding. For now, I'm skeptical, as the first experience has been rather stilted. Oh well. To be continued.
Cheers.